While Multi-tenant Deployments and Elastic and Transient Environments have been a big focus for us here at Octopus in recent times, there's also been some exciting things happening in the areas of Authentication and a new feature we're calling Subscriptions to help you subscribe to events and get notified via email or webhooks as things occur within Octopus.
We removed the download link for Octopus 3.5.0 because we shipped some bugs that prevented some customers from signing in to the Octopus portal. Please download the latest version and use that instead!
Subscriptions
Octopus took another stride in the automation space when we introduced Project Triggers, specifically Automatic Deployment Triggers. One issue we had left to solve was around notifications.
How do I know if my auto-deployment (that triggered at 2am while I was asleep) actually succeeded or failed, without physically logging into Octopus and looking at my dashboard?
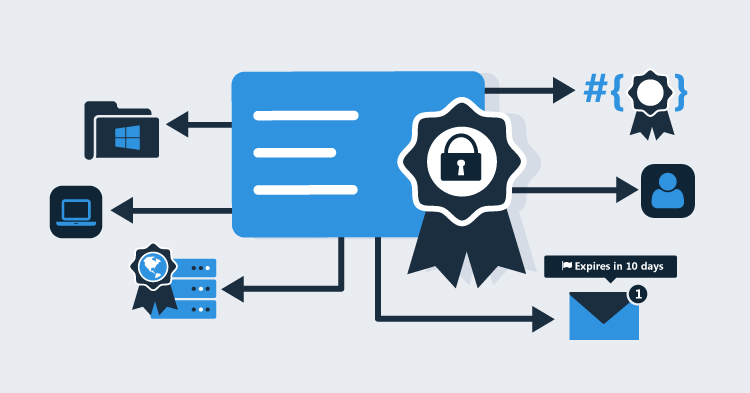
Introducing Octopus Subscriptions, a new feature that allows you to subscribe to events that are happening within Octopus.
You can now setup email or webhook subscriptions and stay informed of any events happening within Octopus. Some obvious examples include:
- deployments succeeding or failing
- manual intervention being required (because of Guided Failures or Manual Intervention steps)
- auto-deployments being blocked and requiring your action
But that's not all! You might just want to be emailed a summary of all events related to your team's environments each day. Or perhaps you'd like to know when Octopus detects your machines going offline or have changes in health. You could even use webhook subscriptions to build your own automated responses to events in Octopus Deploy using the API!
Subscriptions in Octopus Deploy 3.5 leaves it entirely up to your imagination :)
OpenID Connect authentication providers
Up until now Octopus Server has had two authentication modes. One where it handles identity management itself and one where it defers to Active Directory. In v3.5, we've added out-of-the-box support for two OpenID Connect providers, Azure AD and GoogleApps.
An update to Octopus' authentication has been on the radar for a while and we've had requests to add Azure AD and/or Federated Identity support from a number of customers. At Octopus we use GoogleApps for identity management, so it made sense for us to support both of these providers.
Learn more about our Azure AD and GoogleApps support.
Multiple authentication providers
Along with supporting OpenID Connect authentication providers, we now also support enabling more than one authentication provider at a time. I.e. you could have Azure AD, GoogleApps and the UsernamePassword providers all enabled. To support this, some new options have been added to the configure command.
Learn about configuring authentication providers.
Auto Login
While we were in this space, another feature that has been requested is the ability to enable automatic user login. This is for scenarios where there is only a single authentication provider in use, and doesn't require entry of a username/password directly in the Octopus Deploy UI. I.e. either of the OpenID Connect providers or the Active Directory (Domain) provider when Forms Authentication is disabled.
Learn about auto login.
Octopus HA cluster-wide settings and server.config
Several of the settings that we were storing in the server.config XML file have caused minor issues in Octopus HA in the past, when different nodes were inadvertently configured with conflicting settings. Given that the authentication settings were one of the causes, and we were now looking to add more of these, we made the decision to move them to the database.
The migration of this data should be completely transparent. It will happen automatically when the server restarts after the upgrade to 3.5.
For those using configuration management tools such as Chef, Puppet or Desired State Configuration (DSC) directly against the server.config XML file, this will be a breaking change if you depend on the values we've moved.
We hope that any inconvenience caused here will be outweighed by better support for configuration management going forward. To that end, we have added a new show-configuration command to the server.
This command can be used to export XML (that is compatible with the old server.config) to either the console or a specified file. There are also two supported JSON formats for the export, which make using the output nicer in languages like PowerShell and Node.js.
Learn about the show-configuration command.
Octopus Deploy Server Extensibility
It turns out that integrating with Active Directory in a way that will work well across the myriad of different configurations our users have is really, really hard. Having the integration firmly embedded in Octopus Server has also made troubleshooting difficult for both us and our users, and customizations haven't been possible - until now!
We've changed that and we are excited to announce that Octopus Deploy Server is now extensible!
All of the Active Directory integration code has been moved out into an extension that we'll ship out-of-the-box, but will be maintained as open source. So if you need a customized implementation to better suit your environment the path will now be simple. The project is available on Github
The Azure AD and GoogleApps integration is also built as extensions and will be open source. These two are being managed out of a single OpenID Connect related project available on Github
Learn about customizing our extensions or writing your own extensions.
We're interested to see how these new features can help you with your deployment scenarios and look forward to your feedback.
Happy Deployments!